
Joshua Robbins
Welcome to my corner of the digital world!
I write about the things I’m building, learning, breaking and fixing across Computer Science and Cyber Security.
Recent
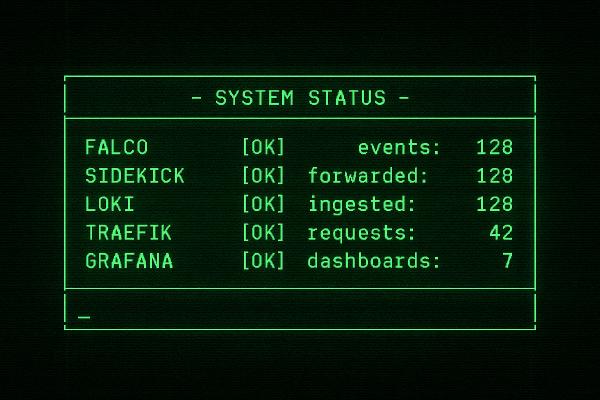
Building a Runtime Container Security Pipeline with Falco, Loki, and Traefik on TrueNAS
·1456 words·7 mins
How I deployed Falco, Sidekick, Loki, and Traefik on TrueNAS to create a secure, real-time container monitoring and alerting pipeline as part of my defense-in-depth strategy.
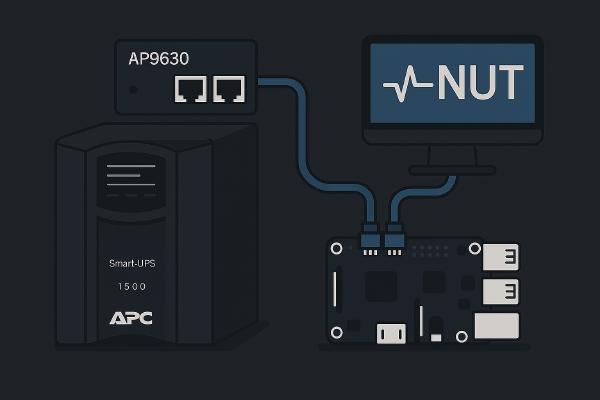
Migrating from USB to SNMP Monitoring with NUT on an APC UPS
·685 words·4 mins
How to compile a modern version of NUT and configure SNMPv3 monitoring for APC UPS systems with AP9630 NMC.

Migrating from Wordpress to Hugo
·851 words·4 mins
A clean, static rebuild of my blog using Hugo replaced the security risks, plugin bloat, and performance issues of WordPress with a fast, version‑controlled, fully automated setup; by building a custom migration pipeline to convert messy WordPress XML into structured Hugo content bundles—with local images, cleaned HTML, converted links, and consistent front matter—I ended up with a secure, future‑proof site that’s easier to maintain and far faster than anything I could achieve on WordPress.

Searching multiple Word documents for keyword
·114 words·1 min
Found myself in a situation I needed to search 20+ documents for a keyword and unfortunately Word cannot search files within a directory for keywords, only the current document

Escalating Privileges to Domain Admin
·211 words·1 min
A quick overview of how local admin rights on a workstation can be misused to escalate privileges when a Domain Admin logs in, along with the reminder that proper least‑privilege policies prevent this risk.